Bachelor of Computer Application (B.C.A.) in CyberSecurity is an undergrad Information Technology course designed to train the students to identify the multidimensional view one would need when it comes to cybersecurity matters. Cybersecurity is an emerging course filled with enthusiastic demand for professionals by various organizations throughout the world. The students are passionate about completing their B.C.A. in cybersecurity from abroad in India. Online institutes have a well-designed cybersecurity course for those planning to get their cybersecurity certificate from a university abroad. The students who are eager about working in cybersecurity can rest easy that on the completion of their course, the job demand will always be high in the market.
The Cybersecurity curriculum trains the learners in various ways in which the students can enhance the security of their organization’s cyberspace and safeguard them against multiple threats in the market. The course teaches us about different emerging technologies present in the market, and one such technology is Cloud Computing. Cloud Computing is tied very often with Cybersecurity due to its vast application in the field of Information Technology. It would not be misleading to say that those students who want to get ahead in cybersecurity should also have a vast knowledge of Cloud Computing.
To summarise Cloud Computing: Cloud computing involves using data storage and computing power of other hardware via the internet, as long as the hardware is connected to the internet. Hence, it would be safe to say that cloud computing is used for tasks that require significantly high computing power. Since organizations use cloud computing, i.e., they use hardware far away connected to the internet, security risks arising from such hardware also need to be considered by the organization.
More about Cybersecurity:
Table of Contents
Cybersecurity consists of protecting internet-connected systems such as hardware, software, and data from cyber threats and cyber-attacks. It refers to the body of technologies, processes, and practices designed to provide security to networks, devices, programs, and data from attack, damage, or unauthorized access.
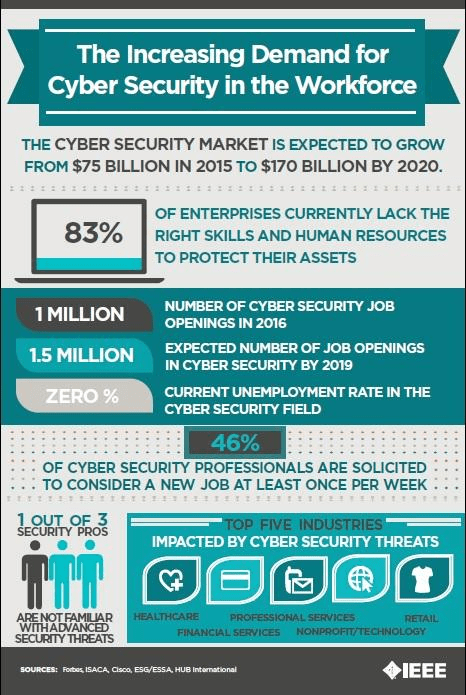
The course of cybersecurity is of great importance as the organizations face the risk of cyber threats and wish to overcome and counter those risks. It is important because a huge amount of data is collected, processed, and stored by various military, medical, corporate and non-corporate, financial and non-financial, government and non-government organizations.
The data so stored may be sensitive, personal, and financial. If unauthorized access were given to such data, it could significantly damage the individuals and the organizations associated with the data. The higher the dependence on computer system infrastructure, the higher is the risk of cyberattacks. New technologies bring newer challenges in the field, and it is of utmost importance that cybersecurity personnel is best equipped and prepared to face these new and emerging challenges.
Cybersecurity is becoming more and more critical due to increased reliance on computer systems, the internet, and wireless network standards such as Bluetooth. The growth of smart devices, which includes smartphones, televisions, and other devices that constitute the internet of things.
Challenges:
Thanks to its complexity, both in terms of politics and technology, cybersecurity is also one of the major challenges in the contemporary world. To be able to secure a computer system, it is vital to understand the attacks that can be made against it, and these threats can typically be classified into one of the following categories given below:
- Backdoors – A secret method of bypassing the normal authentication or security controls
- Denial of Service attack – Attacks that render a machine or a system unavailable or useless to intended users.
- Eavesdropping – Eavesdropping occurs when a person surreptitiously listens to private computer communication between hosts and the network.
Careers:
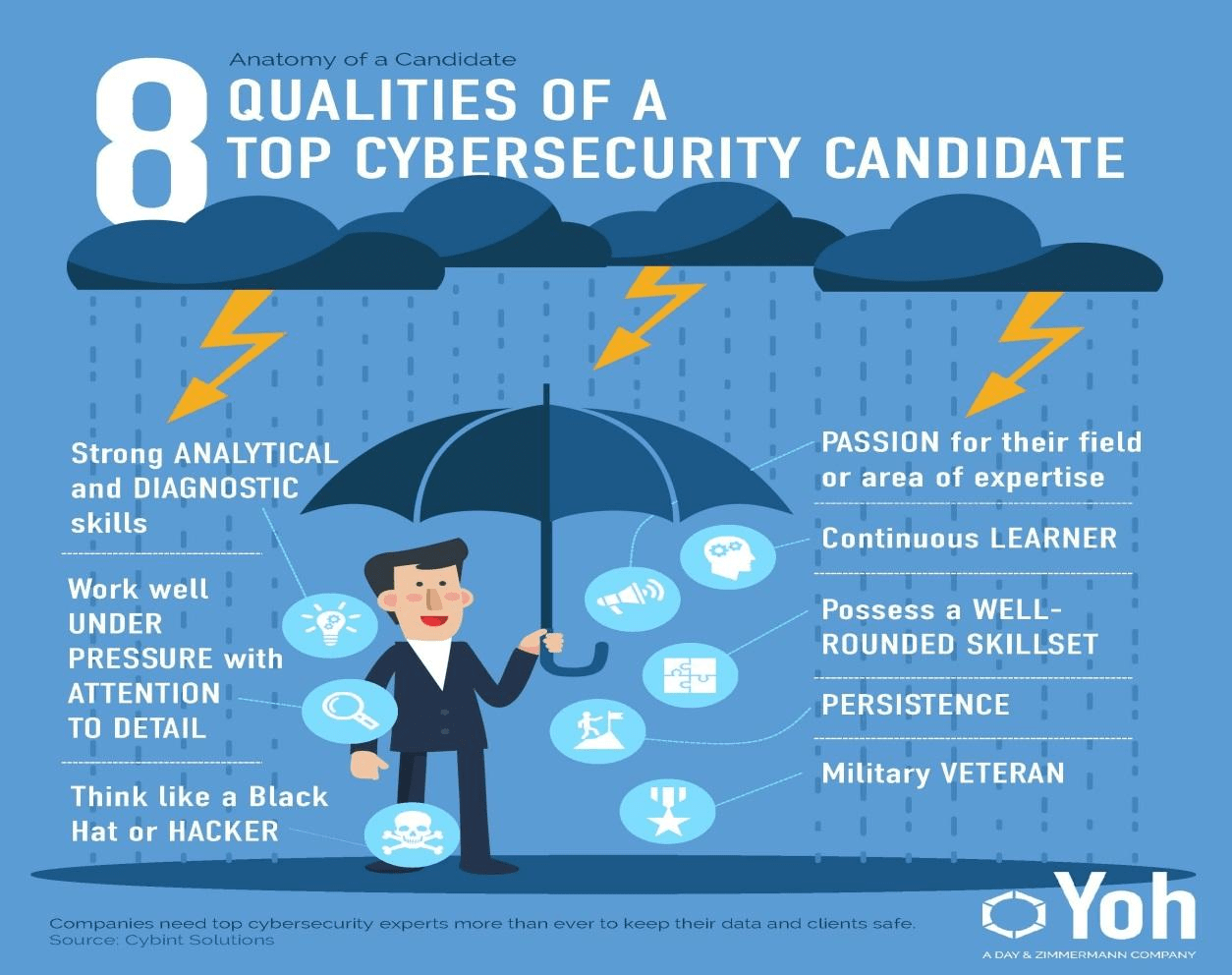
Cybersecurity is one of the fastest-growing information technology fields as concerns about the risk of hack or data breach increase. Organizations always want to ensure that their information assets are well secured and safe from any kind of cyber attack or threat and, consequently, safeguard them from any loss or data breach. According to research, 46% of organizations say that they have a problematic shortage of cybersecurity personnel in 2016, up from 28% in 2015. The various cybersecurity job titles and roles include:
- Security Analyst – A security analyst assesses the vulnerabilities and weaknesses in the infrastructure (software, hardware, and network)and investigates using available tools and countermeasures to remedy the detected vulnerabilities and recommend solutions and best practices.
- Security Engineer – A security engineer performs security monitoring, surveillance, security and data/logs analysis, and forensic analysis to detect security incidents and mounts the incident response. They also implement newer technology to enhance security capabilities and upgrade improvements.
- Chief Information Security Officer – A Chief Security Officer (CISO) is a high-level management position that is responsible for the entire security division or staff.
Frequently Asked Questions (FAQs):
Q1. What is cybersecurity?
Ans: Cybersecurity is the specialization of computer network security that consists of technologies, policies, and procedures that protect networked computer systems from unauthorized use, access, or harm.
Q2. What are cyber-attacks?
Ans: It is an offensive action taken by a malicious person to undermine the functions of networked computer systems and their related resources, including unauthorized access, unapproved changes, and malicious destruction. Some examples are DOS attacks, Backdoors, etc.
Q3. What is a cyber threat?
Ans: A cyber threat is a potential or imminent cyber-attack, which has a higher probability of occurrence as deduced by cyber risk assessment.
Q4. Why do we need cybersecurity?
Ans: The increasing dependence of our information-age economies and governments on computer-based infrastructure makes them more vulnerable to cyber attacks on their computer systems, networks, and data. The cyber threats increase with the introduction and development of new technologies globally, and these could cause significant damage to the informational assets of the government, military, and nation as a whole. Thus, to avoid any such damage, cybersecurity defenses should be upgraded and updated with time and newer technologies.
Q5. What is cyber hygiene?
Ans: Cyber hygiene refers to best practices and activities that computer system administrators and users can undertake to enhance their cybersecurity while engaging in common activities on the internet.
Q6. Is cybersecurity a good career choice?
Ans: As newer technological developments come into the picture, they bring more unknown threats and risks to cybersecurity. Hence, organizations that deal in cybersecurity-related matters like data transmission, collection, etc., are always in dire need of cybersecurity personnel to safeguard their information assets and prevent significant damage to the organization. And hence the market demand for the same is high.
Q7. Who is eligible for the undergraduate course?
Ans: Individuals who have scored 50% or more in their 10th Boards.
Q8. Who is eligible for the postgraduate course?
Ans: Individuals who scored 50% or more in their graduation.